Generate Certificate With Private Key Online
/subway-surfers-free-coins-and-keys-generator-download.html. Generate online private and public key for ssh, putty, github, bitbucket Save both of keys on your computer (text file, dropbox, evernote etc)!!! The generated keys are RANDOM and CAN'T be restored. Generate an ed25519 SSH keypair- this is a new algorithm added in OpenSSH. Ssh-keygen -t ed25519 Extracting the public key from an RSA keypair. Openssl rsa -pubout -in privatekey.pem -out publickey.pem Extracting the public key from an DSA keypair. Openssl dsa -pubout -in privatekey.pem -out publickey.pem Copy the public key to the server. To generate keystores: keytool -genkey -alias server -keyalg RSA -keystore server.jks keytool -genkey -alias client -keyalg RSA -keystore client.jks Getting server's self signed public key certificate and storing it in client's keystore and getting and storing client's self signed public key certificate in server's keystore.
- Generate Certificate With Private Key Online Login
- Generate Certificate With Private Key Online Registration
- Generate A Certificate With Private Key
- How can I find the private key for my SSL certificate. If you just got an issued SSL certificate and are having a hard time finding the corresponding private key, this article can help you to find that one and only key for your certificate.
- Jun 09, 2019 This article describes how to recover a private key after you use the Certificates Microsoft Management Console (MMC) snap-in to delete the original certificate in Internet Information Services (IIS). You delete the original certificate from the personal folder in the local computer's certificate store.
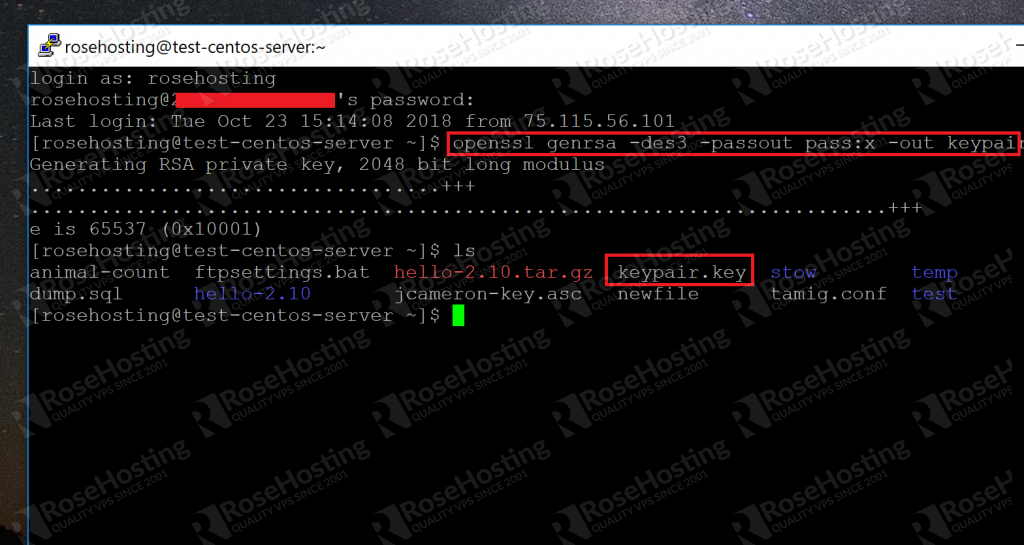
- It fails because code001.private only contains an RSA key, while pkcs12 expects a certificate to go with it. In addition, as said by Stephane, the -nokeys option will cause openssl to skip the private key. You can generate a certificate with. Openssl req -new -x509 -key code001.private -out code001.pem.
A Key Vault (KV) certificate can be either created or imported into a key vault. When a KV certificate is created the private key is created inside the key vault and never exposed to certificate owner. The following are ways to create a certificate in Key Vault:
Create a self-signed certificate: This will create a public-private key pair and associate it with a certificate. The certificate will be signed by its own key.
Create a new certificate manually: This will create a public-private key pair and generate an X.509 certificate signing request. The signing request can be signed by your registration authority or certification authority. The signed x509 certificate can be merged with the pending key pair to complete the KV certificate in Key Vault. Although this method requires more steps, it does provide you with greater security because the private key is created in and restricted to Key Vault. This is explained in the diagram below.

The following descriptions correspond to the green lettered steps in the preceding diagram.
- In the diagram above, your application is creating a certificate which internally begins by creating a key in your key vault.
- Key Vault returns to your application a Certificate Signing Request (CSR)
- Your application passes the CSR to your chosen CA.
- Your chosen CA responds with an X509 Certificate.
- Your application completes the new certificate creation with a merger of the X509 Certificate from your CA.
- Create a certificate with a known issuer provider: This method requires you to do a one-time task of creating an issuer object. Once an issuer object is created in you key vault, its name can be referenced in the policy of the KV certificate. A request to create such a KV certificate will create a key pair in the vault and communicate with the issuer provider service using the information in the referenced issuer object to get an x509 certificate. The x509 certificate is retrieved from the issuer service and is merged with the key pair to complete the KV certificate creation.
Generate Certificate With Private Key Online Login
The following descriptions correspond to the green lettered steps in the preceding diagram.
- In the diagram above, your application is creating a certificate which internally begins by creating a key in your key vault.
- Key Vault sends an TLS/SSL Certificate Request to the CA.
- Your application polls, in a loop and wait process, for your Key Vault for certificate completion. The certificate creation is complete when Key Vault receives the CA’s response with x509 certificate.
- The CA responds to Key Vault's TLS/SSL Certificate Request with an TLS/SSL X.509 certificate.
- Your new certificate creation completes with the merger of the TLS/SSL X.509 certificate for the CA.
Asynchronous process
KV certificate creation is an asynchronous process. This operation will create a KV certificate request and return an http status code of 202 (Accepted). The status of the request can be tracked by polling the pending object created by this operation. The full URI of the pending object is returned in the LOCATION header.
When a request to create a KV certificate completes, the status of the pending object will change to “completed” from “inprogress”, and a new version of the KV certificate will be created. This will become the current version.
First creation
When a KV certificate is created for the first time, an addressable key and secret is also created with the same name as that of the certificate. If the name is already in use, then the operation will fail with an http status code of 409 (conflict).The addressable key and secret get their attributes from the KV certificate attributes. The addressable key and secret created this way are marked as managed keys and secrets, whose lifetime is managed by Key Vault. Managed keys and secrets are read-only. Note: If a KV certificate expires or is disabled, the corresponding key and secret will become inoperable.
If this is the first operation to create a KV certificate then a policy is required. A policy can also be supplied with successive create operations to replace the policy resource. If a policy is not supplied, then the policy resource on the service is used to create a next version of KV certificate. Note that while a request to create a next version is in progress, the current KV certificate, and corresponding addressable key and secret, remain unchanged.
Self-issued certificate
To create a self-issued certificate, set the issuer name as 'Self' in the certificate policy as shown in following snippet from certificate policy.
If the issuer name is not specified, then the issuer name is set to 'Unknown'. When issuer is 'Unknown', the certificate owner will have to manually get a x509 certificate from the issuer of his/her choice, then merge the public x509 certificate with the key vault certificate pending object to complete the certificate creation.
Partnered CA Providers
Certificate creation can be completed manually or using a “Self” issuer. Key Vault also partners with certain issuer providers to simplify the creation of certificates. The following types of certificates can be ordered for key vault with these partner issuer providers.
| Provider | Certificate type |
|---|---|
| DigiCert | Key Vault offers OV or EV SSL certificates with DigiCert |
| GlobalSign | Key Vault offers OV or EV SSL certificates with GlobalSign |
A certificate issuer is an entity represented in Azure Key Vault (KV) as a CertificateIssuer resource. It is used to provide information about the source of a KV certificate; issuer name, provider, credentials, and other administrative details.
Note that when an order is placed with the issuer provider, it may honor or override the x509 certificate extensions and certificate validity period based on the type of certificate.
Authorization: Requires the certificates/create permission.
See Also
You can use this Certificate Key Matcher to check whether a private key matches a certificate or whether a certificate matches a certificate signing request (CSR). When you are dealing with lots of different certificates it can be easy to lose track of which certificate goes with which private key or which CSR was used to generate which certificate. The Certificate Key Matcher tool makes it easy to determine whether a private key matches or a CSR matches a certificate.
The Certificate Key Matcher simply compares a hash of the public key from the private key, the certificate, or the CSR and tells you whether they match or not. You can check whether a certificate matches a private key, or a CSR matches a certificate on your own computer by using the OpenSSL commands below:
openssl pkey -in privateKey.key -pubout -outform pem sha256sum
openssl x509 -in certificate.crt -pubkey -noout -outform pem sha256sum
openssl req -in CSR.csr -pubkey -noout -outform pem sha256sum
Generate Certificate With Private Key Online Registration
Your private key is intended to remain on the server. While we try to make this process as secure as possible by using SSL to encrypt the key when it is sent to the server, for complete security, we recommend that you manually check the public key hash of the private key on your server using the OpenSSL commands above.
You can also do a consistency check on the private key if you are worried that it has been tampered with. See Hanno Böck's article How I tricked Symantec with a Fake Private Key for how to do this and when this might be useful.
Generate A Certificate With Private Key
Save