Ocsp Key And Certificate Request Generation Tool
To Create a CSR with keytool and Generate a SignedCertificate for the Certificate Signing Request
What Is Ocsp
Create and send the OCSP request. To create and send the request you need to use TElFileOCSPClient or TElHTTPOCSPClient components (they are descendants of TElOCSPClient component, which defines most properties and methods). Create an instance of the OCSPClient class of your choice. Online Certificate Status Protocol¶. The Online Certificate Status Protocol (OCSP) was created as an alternative to certificate revocation lists (CRLs). Similar to CRLs, OCSP enables a requesting party (eg, a web browser) to determine the revocation state of a certificate. Online sign the csr and generate x.509 certificate, get a digital certificate from the csr, csr tutorial, openssl csr, generate csr add crl,ocsp.
Ocsp Key And Certificate Request Generation Tool Free
Client sends OCSP request to this proxy server. Initial request contains target certificate's Authority Information Access extension and Issuer field — all as a part of the Service Locator extension. Proxy server uses this information to locate an authoritative OCSP server and sends request to the server. Michael Cobb explains the Certificate Authority Security Council's Online Certificate Status Protocol (OCSP) and OCSP stapling. Such as when the private key associated with a certificate is. Does anybody know of a tool to test OCSP responses? Preferably, something that can be used from a Windows Command-line and/or can be included (easily) in a Java/python program. RFC 6960 PKIX OCSP June 2013 The response for each of the certificates in a request consists of: - target certificate identifier - certificate status value - response validity interval - optional extensions This specification defines the following definitive response indicators for use in the certificate status value: - good - revoked - unknown The 'good' state indicates a positive response to.
Microsoft Ocsp
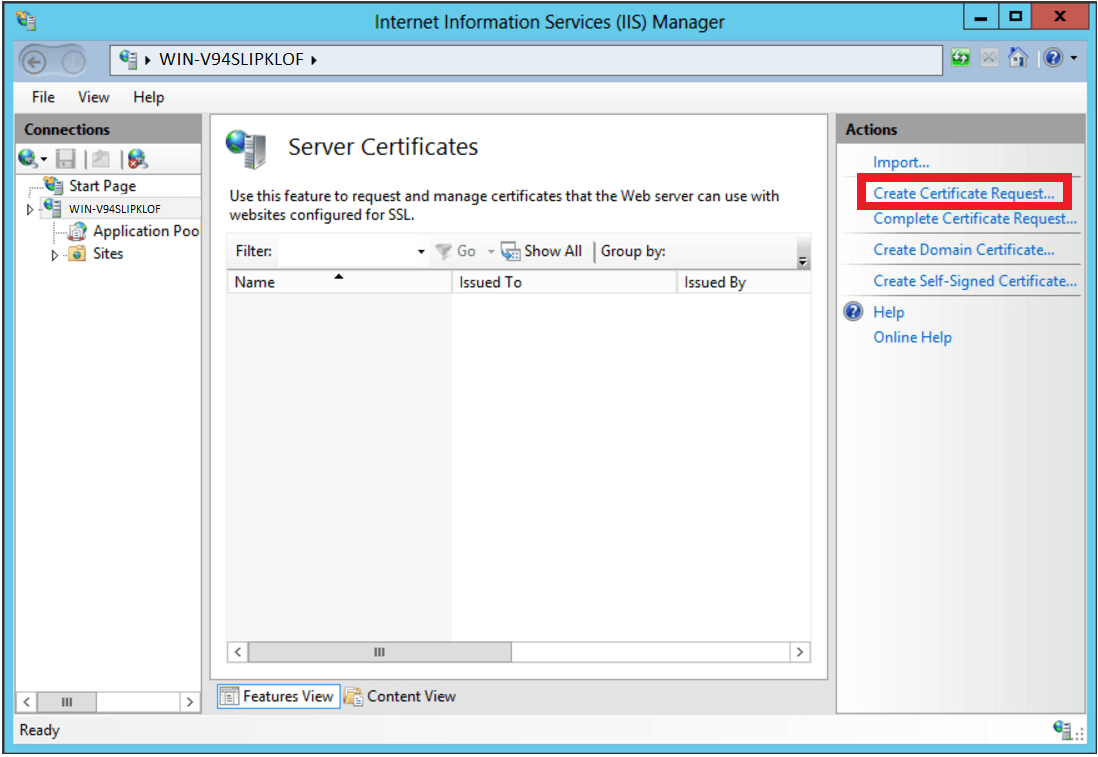
Perform the following operations from the command line.
Generate the Certificate Signing Request.
Generate a signed certificate for the associated Certificate SigningRequest.
Use the keytool to import the CA certificate into the client keystore.
Use the keytool to import the signed certificate for the associatedclient alias in the keystore.
Caution –The following error will be generated if there is no certificatechain in the client certificate.
This error is because the CA’s certificate was not imported intothe KeyStore first. You must import theCA's certificate (step 4), then import the client.cer file itself to forma certificate chain (step 5).
Now that we have a private key and an associating certificate chainin the KeyStore clientkeystore, we canuse it as a KeyStore for client (adapter)authentication. The only warning is that the CA certificate must be importedinto the trusted certificate store of the web server to which you will beconnecting. Moreover, the web server must be configured for client authentication(httpd.conf for Apache, for example).